Can You Spot the Imposter?
July 23, 2020

Over the past few months, we have seen attackers continue to target Biola employees with imposter fraud in the form of phishing emails. Most often, these imposters use sender names as a disguise.
You know to check your emails for phishing indicators like suspicious links, urgent warnings, and strange grammar. You even scrutinize the sender name and signature for warning signs.
Here’s one more tool to protect yourself from phishing: verify the sender’s email address.
The Exploit
For some messages, Gmail will default to only display the sender’s name, not their full email address. If the name shown is someone we recognize or regularly receive email from, we’re likely to open it and respond without scrutiny – but we’re actually responding to the imposter.

Even though this message looks like it’s from Barry Corey, it might not have come from him.
People can choose any sender name they want when sending an email. Attackers use this to their advantage when sending phishing messages.
The Attack
Most imposter fraud attacks don’t include links or other obvious indicators. They begin as short, casual messages. The attackers fake their sender name and email signature to pose as a VP, Dean, or department manager, and then slowly work to convince you that they are who they claim to be.
These attackers rely on the persuasion principle of commitment and consistency. In short, once you respond to their initial request, you’re more likely to follow through with subsequent requests.
After a few emails back and forth, when the attacker has you convinced, they send the phish. It might be a malicious link or an attachment, or a fraudulent money transfer, or a request to purchase gift cards or other digital currency.
Here are two actual Biola examples of how these attacks start out:
From: Dr. xxxxxxxxxx <educationsport12@gmail.com>
To: [Redacted]
Date: May 21, 2020 at 4:29:31 PM PDT
Subject: Special Assignment
Good Morning,
Are you in the office and are you available?
I have an assignment i need you to handle for me.I'm in a meeting and won't be able to pick a call.
Thanks.
From: xxxxxxxxxx <xxxxx.xxxxx.biola.edu@gmail.com>
To: [Redacted]
Date: June 22, 2020 at 2:09:41 PM PDT
Subject: Get back to me!
Send me your available text number!!
--
[Signature redacted]
What You Can Do
Don’t rely on the sender name – instead check the sender address on any email message that looks suspicious, especially if the person sending the message is asking you to do something out of the ordinary.
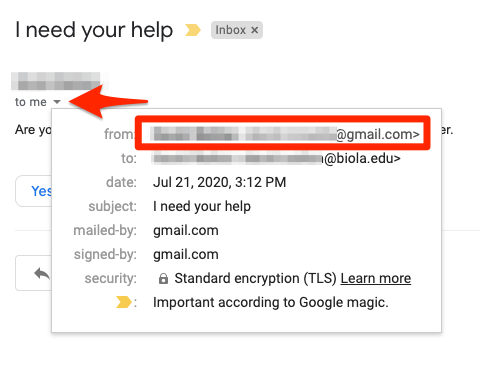
- Click the little triangle arrow to reveal the sender address.
- Verify that the email address is what you expect (Biola addresses end in @biola.edu).
If something’s fishy, don’t reply to the message. Instead, verify the communication by contacting the actual person via another known channel of communication. For example, call them or their administrative assistant at their Biola extension, or copy the request into a new email message and send it to their known Biola email address so that they can verify if it’s legitimate or not.
If you suspect that you or someone else has fallen for an imposter fraud attack, report the incident to information.security@biola.edu.
Phishing has increased during the COVID-19 pandemic. Now, more than ever, we need to stay vigilant and security-minded.
