Where We Stand: Biola InfoSec in 2020
September 30, 2020
Article at a Glance
- Look for our weekly cybersecurity review articles during October.
- Learn how Biola’s cybersecurity awareness has improved from 2018 to 2020.
- See what phishing messages Biolans are most likely to fall for.
All of us have been working intentionally as a community to protect Biola’s data since we began our information security awareness program in October of 2018.
This year, for National Cybersecurity Awareness Month, we'll post weekly updates on My Biola, reviewing core cybersecurity principles. If you’re a new employee at Biola, this will be a great way to get caught up, and if you’ve been around for a few years, it will be a helpful refresher.
To kick things off, let’s review Biola’s cybersecurity progress over the last two years. To measure program success, the InfoSec team looks at the following three areas:
- Employees are recognizing simulated phishing messages.
- Fewer email accounts have been compromised this year.
- Despite COVID-19, more employees completed their mandatory cybersecurity training than last year.
2019 to 2020 – In Detail
Simulated Phishing
We’ve run six simulated phishing campaigns in the last year. Our phishing tool measures how phish-prone Biola employees are as a group. We ran a baseline test in 2019, then ran intermittent campaigns up to now. The table below shows our stats over time:
Year | Phish-Prone Percentage |
|---|---|
2019 Baseline Test | 20.9% |
2020 All Campaigns | 10.5% - 18.6% |
This data encourages us that we’re all getting better at recognizing and rejecting phishing messages. It also tells us that we have room to improve. One way to develop our cybersecurity awareness is to read IT's monthly Information Security articles.
Biolans are particularly susceptible to social engineering emails that appear to be from the government or some “official” entity or office (including court summons, traffic violations, and police investigations).
Here are some examples of the most convincing simulated phishing emails we’ve sent out over the last year:
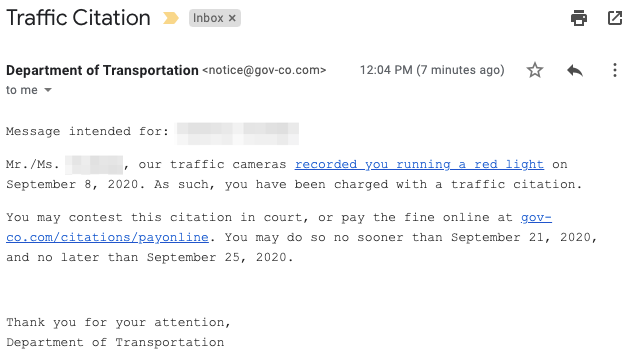
Example 1: Traffic Citation
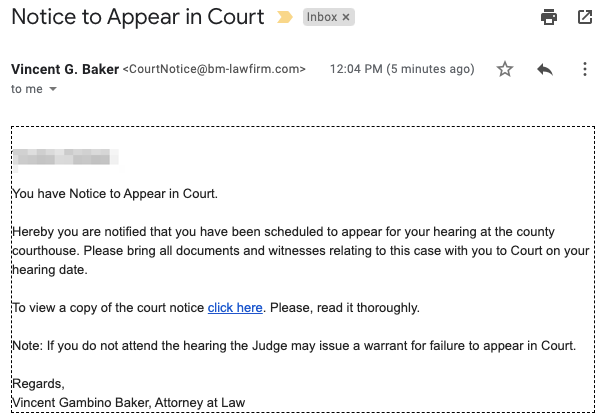
Example 2: Court Summons
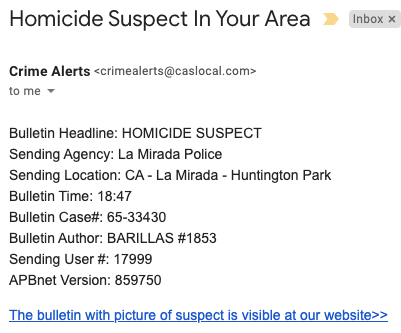
Example 3: Crime Alert
Example 4: Package Delivery Notice
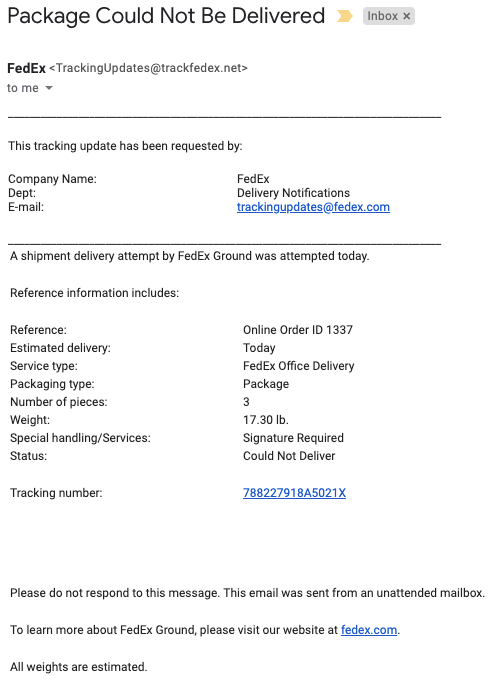
Most of us are able to spot an email with bad graphic design and incorrect product logos. But interestingly, each of the examples above look plain — There are no logos, graphics, or marketing images. This indicates that we’re more likely to trust emails that appear unembellished or bureaucratic.
We are less likely to fall for phishing from technology companies or online services (e.g. a fake Netflix email or Google password reset).
Delivery services also continue to trick us. Two years ago, a Biola department was affected by a Ransomware attack originating from a fake USPS Delivery Notification.
On the positive side, many people are using the Phish Alert Button to report suspicious email messages. Many others are forwarding suspicious messages to phishing@biola.edu. Thank you for contributing to our cybersecurity efforts!
Compromised Email Accounts
We are able to track how many times a Google account is compromised, whether by phishing or some other form of attack.
Here are our compromised account ticket statistics for the last two years:
Year | Compromised Account Tickets |
|---|---|
Oct 2017-2018 | 244 |
Oct 2018-2019 | 34 |
Oct 2019-2020 | 98 |
This data tells us a few things:
- The number of compromised accounts has gone down since we began our Information Security program. Once again: Good job!
- Even though our numbers are lower than in 2017, phishing attacks have increased, not decreased, so we must remain vigilant (especially during the COVID-19 pandemic).
- It is increasingly important for each Biola employee to enable 2-step verification on their Google account. This setting would have prevented every unauthorized login.
Phishing is still our biggest threat. We’ve seen a steady stream of imposter fraud attempts, which are less likely to be flagged by Google’s phishing sensors. The following articles can help refresh you on how to protect Biola against phishing attacks:
- Spot Spoofing Like the Pros
- Hackers Don’t Break In, They Log In
- COVID-19 Scams to Watch Out For
- Don’t Be Manipulated by Social Engineering
Employee Training
If you’re an employee, we assigned your annual cybersecurity training last spring. The online course was required for all full-time and part-time employees (staff and faculty).
Last year, 70% of employees completed their training.
This year, 77% of employees completed their assigned training.
We’re impressed! Spring 2020 was a hectic season, but our completion rate went up from last year. Nice work, Biola!
What’s Next?
For Cybersecurity Awareness Month, we’ll send out weekly updates here and on My Biola.
Each week’s post will include a fun video and a quick review of core cybersecurity principles. Look for our article each week in the Campus-wide News email!
